|
#1
| |||
| |||
|
Will you please give me question paper for NET computer science and application?
|
|
#2
| ||||
| ||||
|
Here I am giving you question paper for NET computer science and application .. 2. The worst case time complexity of AVL tree is better in comparison to binary search tree for (A) Search and Insert Operations (B) Search and Delete Operations (C) Insert and Delete Operations (D) Search, Insert and Delete Operations 3. The GSM network is divided into the following three major systems : (A) SS, BSS, OSS (B) BSS, BSC, MSC (C) CELL, BSC, OSS (D) SS, CELL, MSC 4. The power set of the set {} is (A) {} (B) {, {}} (C) {0} (D) {0, , {}} 5. If the disk head is located initially at 32, find the number of disk moves required with FCFS if the disk queue of I/O blocks requests are 98, 37, 14, 124, 65, 67. (A) 239 (B) 310 (C) 321 (D) 325 6. Component level design is concerned with (A) Flow oriented analysis (B) Class based analysis (C) Both of the above (D) None of the above 7. The ‘C’ language is (A) Context free language (B) Context sensitive language (C) Regular language (D) None of the above 8. The Mobile Application Protocol (MAP) typically runs on top of which protocol ? (A) SNMP (Simple Network Management Protocol) (B) SMTP (Simple Mail Transfer Protocol) (C) SS7 (Signalling System 7) (D) HTTP (Hyper Text Transfer Protocol) COMPUTER SCIENCE AND APPLICATIONS Paper – II Note : This paper contains fifty (50) objective type questions of two (2) marks each. All questions are compulsory. D-87-12 3 Paper-II 9. If a packet arrive with an M-bit value is ‘l’ and a fragmentation offset value ‘0’, then it is ______ fragment. (A) First (B) Middle (C) Last (D) All of the above 10. The number of bit strings of length eight that will either start with a 1 bit or end with two bits 00 shall be (A) 32 (B) 64 (C) 128 (D) 160 11. In compiler design ‘reducing the strength’ refers to (A) reducing the range of values of input variables. (B) code optimization using cheaper machine instructions. (C) reducing efficiency of program. (D) None of the above 12. In which addressing mode, the effective address of the operand is generated by adding a constant value to the contents of register ? (A) Absolute (B) Indirect (C) Immediate (D) Index 13. Which of the following is true ? (A) A relation in BCNF is always in 3NF. (B) A relation in 3NF is always in BCNF. (C) BCNF and 3NF are same. (D) A relation in BCNF is not in 3NF. 14. Given memory partitions of 100 K, 500 K, 200 K, 300 K and 600 K (in order) and processes of 212 K, 417 K, 112 K, and 426 K (in order), using the first-fit algorithm, in which partition would the process requiring 426 K be placed ? (A) 500 K (B) 200 K (C) 300 K (D) 600 K 15. What is the size of the Unicode character in Windows Operating System ? (A) 8-Bits (B) 16-Bits (C) 32-Bits (D) 64-Bits 16. In which tree, for every node the height of its left subtree and right subtree differ almost by one ? (A) Binary search tree (B) AVL tree (C) Threaded Binary Tree (D) Complete Binary Tree 17. The design issue of Datalink Layer in OSI Reference Model is (A) Framing (B) Representation of bits (C) Synchronization of bits (D) Connection control 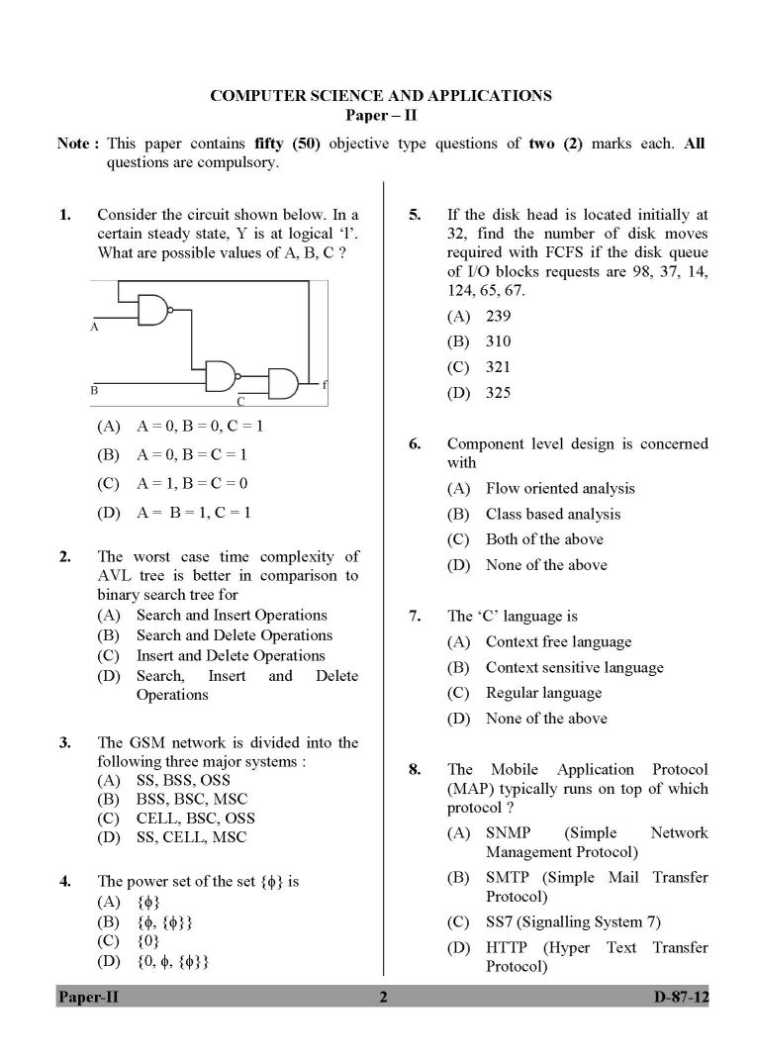     
__________________ Answered By StudyChaCha Member Last edited by Aakashd; August 13th, 2018 at 10:35 AM. |
|
#4
| |||
| |||
|
The National Educational Testing Bureau of University Grants Commission (UGC) conducts National Eligibility Test (NET) for appointment of Lecturers in colleges and universities and for award of Junior Research Fellowship (JRF). Computer Science NET Paper 1. For the 8-bit word 00111001, the check bits stored with it would be 0111. Suppose when the word is read from memory, the check bits are calculated to be 1101.What is the data word that was read from memory? A. 10011001 B. 00011001 C. 00111000 D. 11000110 2. Consider a 32 - bit microprocessor, with a 16 - bit external data bus, driven by an 8 MHz input clock. Assume that the microprocessor has a bus cycle whose minimum duration equals four input clock cycles. What is maximum data transfer rate for this microprocessor ? A. 8 x 106 bytes / sec B. 4 x 106 bytes / sec C. 16 x 106 bytes / sec D. 4 x 109 bytes / sec 3. The RST 7 instruction in 8085 microprocessor is equivalent to A. CALL 0010 H B. CALL 0034 H C. CALL 0038 H D. CALL 003C H 4. The equivalent hexadecimal notation for octal number 2550276 is: A. FADED B. AEOBE C. ADOBE D. ACABE 5. The CPU of a system having 1 MIPS execution rate needs 4 machine cycles on an average for executing an instruction. The fifty percent of the cycles use memory bus. A memory read/write employs one machine cycle. For execution of the programs, the system utilizes 90 percent of the CPU time. For block data transfer, an IO device is attached to the system while CPU executes the background programs continuously. What is the maximum IO data transfer rate if programmed IO data transfer technique is used? A. 500 Kbytes/sec B. 2.2 Mbytes/sec C. 125 Kbytes/sec D. 250 Kbytes/sec 6. The number of Flip-Flops required to design a modulo - 272 counter is A. 8 B. 9 C. 27 D. 11 7. Let E1 and E2 be two entities in E-R diagram with simple single valued attributes. R1 and R2 are two relationships between E1 and E2 where R1 is one-many and R2 is many - many. R1 and R2 donot have any attributes of their own. How many minimum number of tables are required to represent this situation in the relational model ? A. 4 B. 3 C. 2 D. 1 8. The student information in a university is stored in the relation STUDENT (name, sex, marks, dept_Name) Consider the following SQL query select deptName from STUDENT where sex = 'M' group by dept_Name having avg (marks) > (select avg (marks) from STUDENT) It returns the names of the department in which A. the average marks of male students is more than the average marks of the students in the same department B. The average marks of male students is more than the average marks of the students in the university C. The average marks of male students is more than the average marks of male students in the university D. The average marks of students is more than the average marks of male students in the university 9. Which one of the following statements about normal forms is FALSE? A. Lossless, preserving decomposition into 3NF is always possible B. Lossless, preserving decomposition into BCNF is always possible C. Any relation with two attributes is in BCNF D. BCNF is stronger than 3NF 10. The relation vendor order (v_no, v_ord_no, v_name, qty_sup, unit_price) is in 2NF because: A. Non key attribute V_name is dependent on V_no which is part of composite key B. Non key attribute V_name is dependent on qty_sup C. key attribute qty_sup is dependent on primary_key unit price D. key attribute v_ord_no is dependent on primary_key unit price For more questions here I am attaching a pdf file for you so that you can download it. Computer Science NET Paper  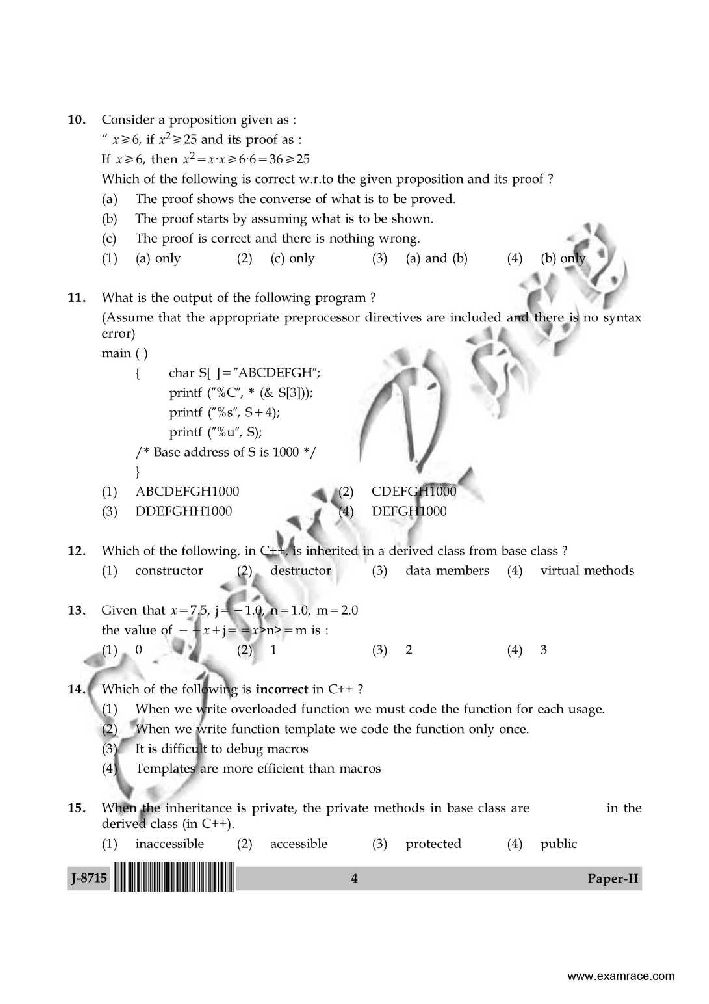 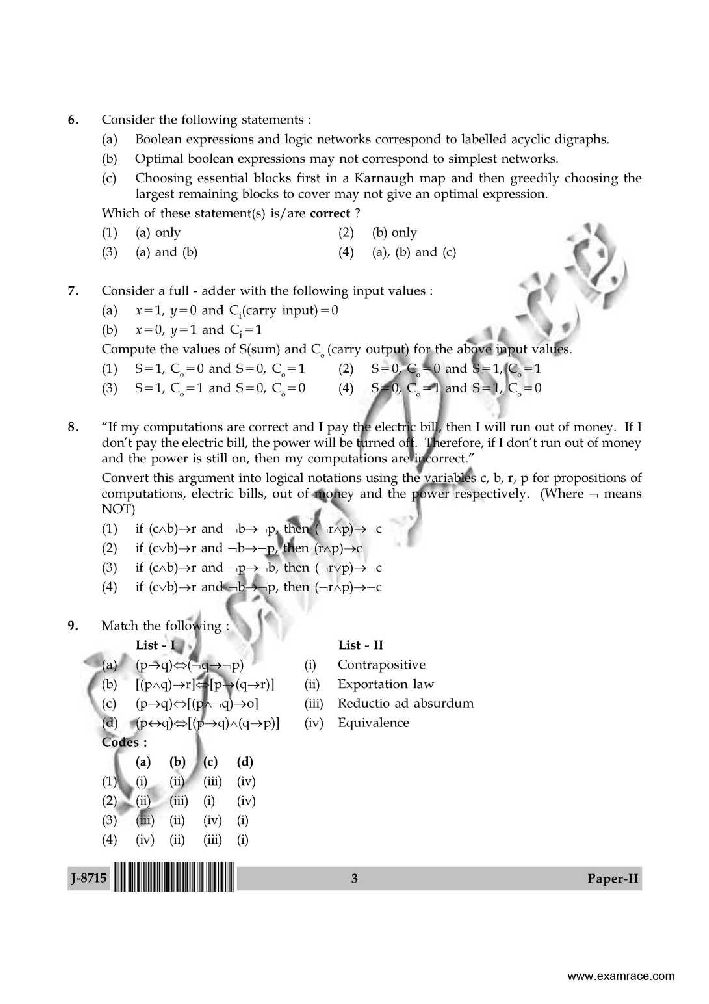 
__________________ Answered By StudyChaCha Member Last edited by Aakashd; August 13th, 2018 at 10:36 AM. |