|
#1
| |||
| |||
|
I am looking for the previous year question papers of Computer Science Engineering of ISRO? Please provide the links? The Indian Space Research Organization is one of the most reputed institutes in India which conducts the majority of the space related researches of the various space programmes of the country. Sample Questions: Two signals of 2GHz and 4GHz are frequency modulated on same carrier 10 GHz. Find the ratio of frequency deviation if band widths of both are equal. a ) 1:2 b)2:1 c) 1:1 d) 1:4 Gray code of 111 is 3X512+7X64+5X8+3 then value in binary form contains _______ number of 1?s. a) 7 b) 6 c) 9 d) none The 2?s compliment of decimal number 19 in 8-bit system is The high gain codes are a) Turbo codes b) BCH codes c) R-S codes BCH codes are of the type________ a) Convolutional type b) c) 8) Time constant of LC circuit is a) L/R b) L/R2 c) RL If R is doubled and C is halved then frequency of series RLC circuit is 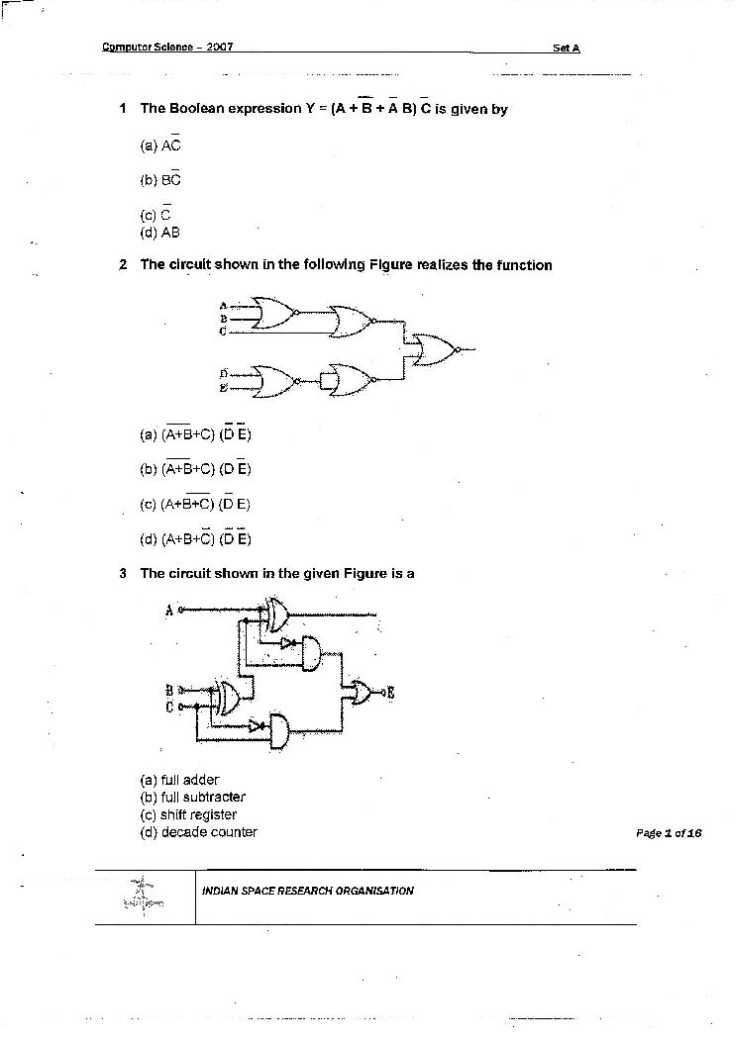      Here I am attaching the previous year question papers of the ISRO CSE Exam Last edited by Aakashd; June 11th, 2019 at 12:03 PM. |
|
#2
| |||
| |||
|
You need ISRO Computer Science Engineering Question paper, I am providing here: ISRO CSE paper 1. Which of the following features usually applies to data in a data warehouse? (a) Data are often deleted (b) Most applications consists of transactions (c) Data are rarely deleted (d) Relatively few records are processed by applications (e) None of these 2. Which of the following is a transaction? (a) A group of SQL statements consisting of one read and one write operation (b) A group of SQL statements consisting only of ready operations. (c) A group of SQL statements defining a user-oriented task (d) A group of SQL statements consisting only of write operations. (e) None of these 3. There are several security devices used to stop individuals from exploiting your system. Which of the following is used in conjunction with a firewall? (a) Proxy server (b) Intrusion- detection system (c) Terminal server (d) Web server (e) None of these 4. The effect of the ROLLBACK command in a transaction is the following…… (a) Undo all changes to the data- base resulting from the execution of the transaction (b) Undo the effects of the last UPDATE command (c) Restore the content of the database to its state at the end of the previous day (d) Make sure that all changes to the database are in effect (e) None of these 5. A client / server network ………. (a) has clients that provide functions such as application control and shared computation. (b) uses client computers to provide copies of software to the server to allow server processing. (c) provides a company with the capability to downsize from lager computer systems and move away from legacy systems. (d) has server computers that perform all processing, clients are’ dumb’ input/ output devices only. (e) None of these. 6. An applet is ……. Document application program. (a) a static (b) a dynamic (c) an active (d) a passive (e) None of these 7. The local antenna for satellite connections is called a …….. (a) modem (b) terminal (c) VSAT (d) DTA (e) None of these 8. What are the four basis connecting hardware devices? (a) Repeater, bridge, router and gateway (b) Repeater, bridge, router and dell (c) Repeater, connector, router and gateway (d) Amplifier, bridge, router and gateway (e) None of these 9. Which type of processing speed measurement is used primarily with supercomputers? (a) Flops (b) Fractions of second (c) Gigahertz (d) MIPS (e) None of these 10. This type of software is designed for users who want to customize the programs they use. (a) Shareware (b) Open-source software (c) Freeware (d) Macros (e) None of these 11. What is the term associated with the second part of an e-mail address? (a) Local address (b) Eight characters long (c) User name (d) Domain name (e) None of these 12. A port that allows 8 bits at a time to be transmitted simultaneously is a (n) ….. (a) dedicated port (b) parallel port (c) SCSI port (d) USB port (e) None of these 13. In order for computers to communicate across a network, they must be connected through a(n)….. (a) TCP/IP (b) Topology (c) Ethernet (d) Thin client (e) None of these (e) C. Rangarajan 14. What is a specialized software program that allows input and output devices to communicate with the rest of the computer system? (a) Utility driver (b) Utility program (c) Data compression utility (d) Device driver (e) None of these 15. Single party disk relying on the disk controller for finding out which disk has failed is used by- (a) RAID level 5 (b) RAID level 2 (c) RAID level 4 (d) RAID level 3 (e) RAID level 1 16. Which of these terms refers to the feature of an OS that allows a single computer to process the tasks of several users at different stations, in round-robin fashion? (a) Multiprocessing (b) Multiprogramming (c) Multitasking (d) Time processing (e) Time-sharing 17. Which of the following statements is not true about two-tier client-server database architecture? (a) SQL statements are processed on the server (b) SQL statements may be processed on some of the clients (c) Business logic is mostly processed on clients (d) Business logic may be processed on the server (e) None of these 18. A Relational operator that yields all values from selected attributes is known as a – (a) difference (b) product (c) select (d) project (e) join 19. Normalization is: (a) the process of creating small stable data structures from complex groups of data when designing a relational database (b) a methodology for documenting database illustrating the relationship between various entities in the database (c) an approach to data management that stores both data and the procedures acting on the data as object that can be automatically retrieved and shared (d) a representation of data as they would appear to an application programmer or user (e) a representation of data as they actually would be organized on physical storage media 20. The process of building a model that demonstrate the features of a proposed product, service or system is called a – (a) JAD (b) RAD (c) templating (d) prototyping (e) TAD 21. Which of the following is mandatory component of a URL? (a) Resource Path (b) Protocol (c) Port Number (d) Domain Name (e) None of these 22. DBMS allows you to extrapolate information from your data by using a- (a) query language (b) table generator (c) report generator (d) wizard (e) None of these 23. A subschema is – (a) a description of the physical and logical structure of data and the relationship among the data (b) a file that identifies the subset of data that a group of users can access (c) a detailed description of all data contained in the database (d) a description of the types of modifications that users can make to a database (e) Either (c) or (d) 24. Which of the following is not a type of hub? (a) Passive hub (b) Inactive hub (c) Switching hub (d) Intelligent hub (e) None of these 25. The ……….. lists the location of files on the disk (a) FAT (b) boot sector (c) root folder (d) data area (e) None of these Answers: 1. (b) 2. (a) 3. (a) 4. (a) 5. (b) 6. (b) 7. (e) 8. (a) 9. (a) 10. (a) 11. (d) 12. (b) 13. (b) 14. (d) 15. (d) 16. (e) 17. (c) 18. (d) 19. (a) 20. (d) 21. (e) 22. (a) 23. (e) 24. (b) 25. (a) 1. Simplify the Boolean expression XY′Z′+XY′Z′W+XZ′ The above expression can be written as XY′Z′ (1+W) +XZ′ =XY′Z′+XZ′ as 1+W=1 =XZ′ (Y′+1) =XZ′ as Y′+1=1 2. Simplify the Boolean expression X+X′Y+Y′+(X+Y′) X′Y The above expression can be written as X+X′Y+Y′+XX′Y+Y′X′Y =X+X′Y+Y′ as XX′=0, and YY′=0 =X+Y+Y′ as X+X′Y=X+Y =X+1 as Y+Y′=1 =1 as X + 1=1 3. Simplify the Boolean expression Z(Y+Z) (X+Y+Z) The above expression can be written as (ZY+ZZ)(X+Y+Z) = (ZY+Z) (X+Y+Z) as ZZ=Z =Z(X+Y+Z) as Z+ZY=Z =ZX+ZY+ZZ =ZX+ZY+Z as ZZ=Z, =ZX+Z as Z+ZY=Z =Z as Z+ZX=Z 4. Simplify the Boolean expression (X+Y)(X′+Z)(Y+Z) The above expression can be written as (XX′+XZ+YX′+YZ)(Y+Z) =(XZ+YX′+YZ) (Y+Z) as XX′=0 =XZY+YYX′+YYZ+XZZ+YX′Z+YZZ =XZY+YX′+YZ+XZ+YX′Z+YZ as YY=Y, ZZ=Z Rearranging the terms we get XZY+XZ+YX′+YX′Z+YZ as YZ+YZ=YZ =XZ(Y+1) +YX′+YZ (X′+1) as Y+1=1, X′+1=1 =XZ+YX′+YZ Now it seems that it cannot be reduced further. But apply the following trick: The above expression can be written as XZ+YX′+YZ(X+X′) as X+X′=1 =XZ+YX′+YZX+YZX′ Rearranging the terms we get XZ+YXZ+Y X′+YX′Z =XZ (1+Y) +YX′ (1+Z) =XZ+YX′ as 1+Y=1, 1+Z=1 _ _ _ 1. The Boolean expression Y = (A + B + AB) C is given by _ (a) AC _ (b) BC _ (c) C (d) AB 2. The circuit shown in the following Figure realizes the function ___ _ _ (a) (A+B+C) (D E) ___ _ (b) (A+B+C) (D E) ___ _ (c) (A+B+C) (D E) _ _ _ (a) (A+B+C) (D E) 3. The circuit shown in the given Figure is a (a) full adder (b) full subtracter (c) shift register (d) decade counter 4. When two numbers are added in excess-3 code and the sum is less than 9, then in order to get the correct answer it is necessary to (a) subtract 0011 from the sum (b) add 0011 to the sum (c) subtract 0110 from the sum (d) add 0110 to the sum 5. The characteristic equation of an SR flip-flop is given by 6. A grap with "n" vertices and n-1 edges that is not a tree, is (a) Connected (b) Disconnected (c) Euler (d) A circuit 7. If a graph requires k different colours for its proper colouring, the the chromatic number of the graph is (a) 1 (b) k (c) k-1 (d) k/2 8. A read bit can be read (a) and written by CPU (b) and written by peripheral (c) by pheripheral and written by CPU (d) by CPU and written by the peripheral 9. Eigen vectors of 10. The term "aging" refers to (a) booting up the priority of a process in multi-level of queue without feedback. (b) gradually increasing the priority of jobs that wait in the system for a long time to remedy infinite blocking. (c) keeping track of the following a page has been in memory for the purpose of LRU replacement (d) letting job reside in memory for a certain amount of time so that the number of pages required can be estimated accurately. 11. Consider a set of n tasks with known runtimes r1, r2 ......... rn, to be run on a uniprocessor machine. Which of the following processor scheduling algorithms will result in the ma throughput ? (a) Round Robin (b) Shortest job first (c) Highest response ratio next (d) first cum first served 12. Consider a job scheduling problem with four jobs J1 J2 J3 and J4 with corresponding deadlines : (d1, d2, d3, d4) = (4,2,4,2) Which of the following is not a feasible schedule without violating any job deadline ? (a) J2, J4, J1, J3 (b) J4, J1, J2, J3 (c) J4, J2, J1, J3 (d) J4, J2, J3, J1 13. By using an eight bit optical encoder the degree of resolution that can be obtained is (approximately) (a) 1.80 (b) 3.40 (c) 2.80 (d) 1.40 14. The principal of locality of reference justifies the use of (a) virtual memory (b) interrupts (c) main memory (d) cache memory 15. Consider the following psuedocode x : = 1; i : = 1; while (x ≤ 1000) begin x : = 2x ; i : = i + 1 ; end ; What is the value of i at the end of the pseudocode ? (a) 4 (b) 5 (c) 6 (d) 7 16. The five items : A, B, C, D, and E are pushed in a stack, one after the other starting from A. The stack is popped four times and each element is inserted in a queue. Then two elements are deleted from the queue and pushed back on the stack. Now one item is popped from the stack. The popped item is (a) A (b) B (c) C (d) D 17. Round Robin scheduling is essentially the pre-emptive version of (a) FIFO (b) Shortest Job First (c) Shortest remaining time (d) Longest remaining time 18. The number of digit 1 present in the binary representation of 3 * 512 + 7 * 64 + 5 * 8 + 3 is (a) 8 (b) 9 (c) 10 (d) 12 19. Assume that each character code consists of 8 bits. The number of characters that can be transmitted per second through an synchronous serial line at 2400 baud rate, and with two stop bits is (a) 109 (b) 216 (c) 218 (d) 219 20. If the bandwidth of a signal is 5 kHz and the lowest frequency is 52 kHz, what is the highest frequency (a) 5 kHz (b) 10 kHz (c) 47 kHz (d) 57 kHz 21. An Ethernet hub (a) functions as a repeater (b) connects to a digital PBX (c) connects to a token-ring network (d) functions as a gateway 22. Phase transition for each bit are used in (a) Amplitude modulation (b) Carrier modulation (c) Manchester encoding (d) NRZ encoding 23. Study the following programme // precondition : x > = 0 public void demo (int x) { System.out.print(x%10); if ((x/10) ! = 0) { demo(x/10); } System.out.print(x%10); } Which of the following is printed as a result of the call demo (1234) ? (a) 1441 (b) 3443 (c) 12344321 (d) 43211234 24. Bit stuffing refers to (a) inserting a '0' in user stream to differentiate it with a flag (b) inserting a '0' in flag stream to avoid ambiguity (c) appending nibble to the flag sequence (d) appending a nibble to the use data stream 25. What is the name of the technique in which the operating system of a computer executes several programs concurrently by switching back and forth between them ? (a) Partitioning (b) Multi tasking (c) Windowing (d) Paging 26. If there are five routers and six networks in an intranet using link state routing, how many routing tables are there ? (a) 1 (b) 5 (c) 6 (d) 11 27. Virtual memory is (a) Part of Main Memory only used for swapping (b) A technique to allow a program, of size more than the size of the main memory, to run (c) Part of secondary storage used in program execution (d) None of these 28. The level of aggregation of information required for operational control is (a) Detailed (b) Aggregate (c) Qualitative (d) None of the above 29. The set of all Equivalence Classes of a set A of Cardinality C (a) is of cardinality 20 (b) has the same cardinality as A (c) forms a partition of A (d) is of cardinality C2 30. 0.75 in decimal system is equivalent to __________ in octal system (a) 0.60 (b) 0.52 (c) 0.54 (d) 0.50 31. In an SR latch made by cross coupling two NAND gates, if both S and R inputs are set to 0, then it will result in (a) Q = 0, Q0 = 1 (b) Q = 1, Q0 = 0 (c) Q = 1, Q0 = 1 (d) Indeterminate states 32. Identify the correct translation into logical notation of the following assertion. Some boys in the class are taller than all the girls Note: taller (x,y) is true if x is taller than y. image - Computer Science - 2007 -Set A - Qno. 32 (a, b, c, d) 33. Company X shipped 5 computer chips, 1 of which was defective, and Company Y shipped 4 computer chips, 2 of which were defective. One computer chip is to be chosen uniformly at random from the 9 chips shipped by the companies. If the chosen chip is found to be defective, what is the probability that the chip came from Company Y ? (a) 2/9 (b) 4/9 (c) 2/3 (d) 1/2 34. Ring counter is analogous to (a) Toggle Switch (b) Latch (c) Stepping Switch (d) S-R flip flop 35. The output 0 and 1 level for TTL Logic family is approximately (a) 0.1 and 5 V (b) 0.6 and 3.5 V (c) 0.9 and 1.75 V (d) -1.75 and 0.9 V 36. Consider a computer system that stores floating-point numbers with 16-bit mantissa and an 8-bit exponent, each in two's complement. The smallest and largest positive values which can be stored are (a) 1 * 10-128 and 215 * 10128 (b) 1 * 10-256 and 215 * 10255 (c) 1 * 10-128 and 215 * 10127 (d) 1 * 10-128 and (215 - 1) * 10127 37. In comparison with static RAM memory, the dynamic RAM memory has (a) lower bit density and higher power consumption (b) higher bit density and higher power consumption (c) lower bit density and lower power consumption (d) higher bit density and lower power consumption 38. The Hexadecimal equivalent of 01111100110111100011 is (a) CD73E (b) ABD3F (c) 7CDE3 (d) FA4CD 39. Disk requests are received by a disk drive for cylinder 5, 25, 18, 3, 39, 8 and 35 in that order. A seek taken 5 msec per cylinder moved. How much seek time is needed to serve these requests for a Shortest Seek First (SSF) algorithm ? Assume that the arm is at cylinder ?, 0 when the last of these requests is made with none of the requests yet served (a) 125 msec (b) 295 msec (c) 575 msec (d) 750 msec 40. Consider a system having 'm' resources of the same type. The resources are shared by 3 processes A, B, C, which have peak time demands of 3, 4, 6, respectively. The minimum value of 'm' that ensures that deadlock will never occur is (a) 11 (b) 12 (c) 13 (d) 14 41. A task in a blocked state (a) is executable (b) is running (c) must still be placed in the run queues (d) Is waiting for some temporarily unavailable resources. 42. Semaphores (a) synchronize critical resources to prevent deadlock (b) synchronize critical resources to prevent contention (c) are used to do I/O (d) are used for memory management. 43. On a system using non-preemptive scheduling, processes with expected run times of 5, 18, 9 and 12 are in the ready queue. In what order should they be run to minimize wait time ? (a) 5, 12, 9, 18 (b) 5, 9, 12, 18 (c) 12, 18, 9, 5 (d) 9, 12, 18, 5 44. The number of page frames that must be allocated to a running process in a virtual memory environment is determined by (a) the instruction set architecture (b) page size (c) number of processes in memory (d) physical memory size 45. A program consists of two modules executed sequentially. Let f1 (t) and f2 (t) respectively denote the probability density functions of time taken to execute the two modules. The probability density function of the overall time taken to execute the program is given by (a) f1 (t) + f2 (t) (b) ∫01 f1 (x)f2 (x) dx (c) ∫01 f1 (x) f2 (t - x) dx (d) max (f1 (t) + f2 (t)) 46. Consider a small 2-way set associative cache memory, consisting of four blocks. For choosing the block to be replaced, use the least recently (LRU) scheme. The number of cache misses for the following sequence of block addresses is 8, 12, 0, 12, 8 (a) 2 (b) 3 (c) 4 (d) 5 47. Which commands are used to control access over objects in relational database ? (a) CASCADE & MVD (b) GRANT & REVOKE (c) QUE & QUIST (d) None of these 48. Which of the following is aggregate function in SQL ? (a) Avg (b) Select (c) Ordered by (d) distinct 49. One approach to handling fuzzy logic data might be to design a computer using ternary (base-3) logic so that data could be stored as "true," "false," and "unknown." If each ternary logic element is called a flit, how many flits are required to represent at least 256 different values ? (a) 4 (b) 5 (c) 6 (d) 7 50. A view of a database that appears to an application program is known as (a) Schema (b) Subschema (c) Virtual table (d) None of these 51. Armstrong's inference rule doesn't determine (a) Reflexivity (b) Augmentation (c) Transitivity (d) Mutual dependency 52. Which operation is used to extract specified columns from a table ? (a) Project (b) Join (c) Extract (d) Substitute 53. In the Big-Endian system, the computer stores (a) MSB of data in the lowest memory address of data unit (b) LSB of data in the lowest memory address of data unit (c) MSB of data in the highest memory address of data unit (d) LSB of data in the highest memory address of data unit 54. BCNF is not used for cases where a relation has (a) Two (or more) candidate keys (b) Two candidate keys and composite (c) The candidate key overlap (d) Two mutually exclusive foreign keys 55. Selection sort algorithm design technique is an example of (a) Greedy method (b) Divide-an-conquer (c) Dynamic Programming (d) Backtracking 56. Which of the following RAID level provides the highest Data Transfer Rate (Read/Write) (a) RAID 1 (b) RAID 3 (c) RAID 4 (d) RAID 5 57. Which of the following programming language (s) provides garbage collection automatically (a) Lisp (b) C++ (c) Fortran (d) C 58. The Average case and worst case complexities for Merge sort algorithm are (a) O (n2), O (n2) (b) O (n2), O (n log2 n) (c) O (n log2 n), O (n2) (d) O (n log2 n), O (n log2 n) 59. The time taken by binary search algorithm to search a key in a sorted array of n elements is (a) O (log2 n) (b) O (n) (c) O (n log2 n) (d) O (n2) 60. Which of the following is correct with respect to Two phase commit protocol ? (a) Ensures serializability (b) Prevents Deadlock (c) Detects Deadlock (d) Recover from Deadlock 61. The Fibonacci sequence is the sequence of integers (a) 1, 3, 5, 7, 9, 11, 13 (b) 0, 1, 1, 2, 3, 5, 8, 13, 21, 54 (c) 0, 1, 3, 4, 7, 11, 18, 29, 47 (d) 0, 1, 3, 7, 15 62. Let X be the adjacency matrix of a graph G with no self loops. The entries along the principal diagonal of X are (a) all zeros (b) all ones (c) both zeros and ones (d) different 63. Which of these is not a feature of WAP 2.0 (a) Push & Pull Model (b) Interface to a storage device (c) Multimedia messaging (d) Hashing 64. Feedback queues (a) are very simple to implement (b) dispatch tasks according to execution characteristics (c) are used to favour real time tasks (d) require manual intervention to implement properly 65. Which of the following is not a UML DIAGRAM ? (a) Use Case (b) Class Diagram (c) Analysis Diagram (d) Swimlane Diagram 66. Silly Window Syndrome is related to (a) Error during transmission (b) File transfer protocol (c) Degrade in TCP performance (d) Interface problem 67. To execute all loops at their boundaries and within their operational bounds is an example of (a) Black Box Testing (b) Alpha Testing (c) Recovery Testing (d) White Box Testing 68. SSL is not responsible for (a) Mutual authentication of client & server (b) Secret communication (c) Data Integrity protection (d) Error detection & correction 69. A rule in a limited entry decision table is a (a) row of the table consisting of condition entries (b) row of the table consisting of action entries (c) column of the table consisting of condition entries and the corresponding action entries (d) columns of the table consisting of conditions of the stub 70. The standard for certificates used on internet is (a) X.25 (b) X.301 (c) X.409 (d) X.509 71. Hashed message is signed by a sender using (a) his public key (b) his private key (c) receiver's public key (d) receiver's private key 72. An email contains a textual birthday greeting, a picture of a cake, and a song. The order is not important. What is the content-type ? (a) Multipart/mixed (b) Multipart/parallel (c) Multipart/digest (d) Multipart/alternative 73. Range of IP Address from 224.0.0.0 to 239.255.255.255 are (a) Reserved for loopback (b) Reserved for broadcast (c) Used for muticast packets (d) Reserved for future addressing 74. IEEE 802.11 is standard for (a) Ethernet (b) Bluetooth (c) Broadband Wireless (d) Wireless LANs 75. When a host on network A sends a message to a host on network B, which address does the router look at ? (a) Port (b) IP (c) Physical (d) Subnet mask 76. Which of the following is not an approach to Software Process Assessment ? (a) SPICE(ISO/IEC 15504) (b) Standard CMMI Assessment Method for process improvement (c) ISO 9001 : 2000 (d) IEEE 2000 : 2001 77. A physical DFD specifies (a) what processes will be used (b) who generates data and who processes it (c) what each person in an organization does (d) which data will be generated 78. In UML diagram of a class (a) state of object cannot be represented (b) state is irrelevant (c) state is represented as an attribute (d) state is represented as a result of an operation 79. Which of the following models is used for software reliability ? (a) Waterfall (b) Musa (c) COCOMO (d) Rayleigh 80. Djikstra's algorithm is used to (a) Create LSAs (b) Flood an internet with information (c) Calculate the routing tables (d) Create a link state database
__________________ Answered By StudyChaCha Member |